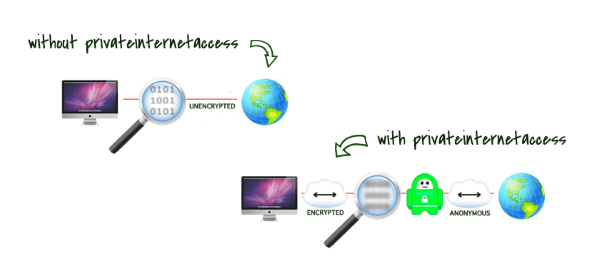
Everything you do on your Internet connection, can be seen by your ISP. That information, while you might not care who sees it, is about to become a commodity to be sold and utilized in ways you might not approve of.
This Category contains techy blogs The Computer Peeps have posted.

Everything you do on your Internet connection, can be seen by your ISP. That information, while you might not care who sees it, is about to become a commodity to be sold and utilized in ways you might not approve of.

AOL is reporting a massive data breach which affects a “significant amount of users”. AOL is recommending users change their passwords immediately.
According to AOL’s Security Team:
This information included AOL users’ email addresses, postal addresses, address book contact information, encrypted passwords and encrypted answers to security questions that we ask when a user resets his or her password, as well as certain employee information. We believe that spammers have used this contact information to send spoofed emails that appeared to come from roughly 2% of our email accounts.
If you utilize AOL for your consignment software’s email functionality, or for your personal email, please be sure to change your password right away.

Stunnel, an application that provides secure ‘tunneling’ for commonly used, insecure protocols (e.g. SMTP, POP3, etc.) has issued a security bulletin.