The Biebs. The Biebs. This latest social engineering attack comes by way of Justin Bieber and a “video that ends his career for good.” I guess these sorts of links are irresistible too. It’s the guys clicking this one! 😀
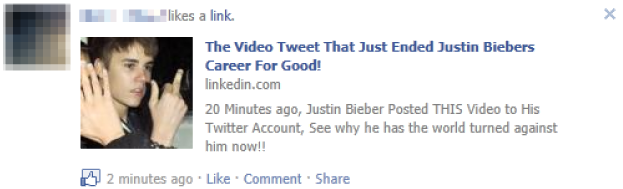
We’re *all adults, so I’m not going to blur out the middle finger. 😀 Ok, so I have to give *them* some credit on this one. In Facebook posts, they always show the domain name – e.g. in this case, linkedin.com. If you hover your cursor above the link though, it reveals the following:

The LinkedIn domain name is completely legitimate! There’s actually a *flaw* of sorts in LinkedIn’s code. The redirect?url= variable accepts any URL, as long as it begins with www. So I’m able to enter http://www.linkedin.com/redirect?url=www.thecomputerpeeps.com and it will take you to our website.
Someone noticed this and realized, “hey, Facebook only shows the domain name.” They take you off to their site and launch a screen shot of a Justin Bieber video, re-post to your Facebook wall and write a virus to your hard disk…
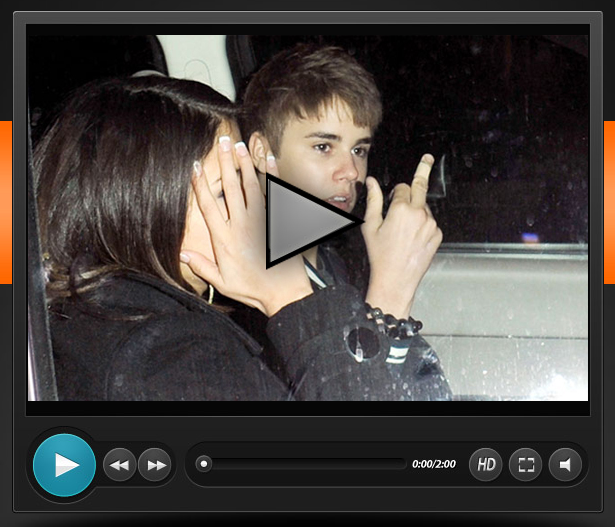
Well, since LinkedIn is a legit site, Facebook is going to let it slide. Yikes! So really, this issue begins with LinkedIn’s system.
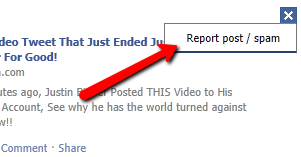
When you see this post, mark it as SPAM…
Not even a week from our Social Media Frenzy workshop in Dallas and we see a new, smarter malware post. I was discussing this with Kate Holmes and a good way to explain this, is to equate it to the flu shot. Without people poking around and finding all of these flaws, systems would remain insecure and vulnerable to attack.
If you or anyone you know clicked on that link out there in the Facebook Feed, your system is infected (if it didn’t pop-up a quarantine notification right away). You know the drill -> http://mycp.biz/thecomputerpeeps_eset.
Don’t forget to read our other posts that show other types of Facebook social engineering attacks.

