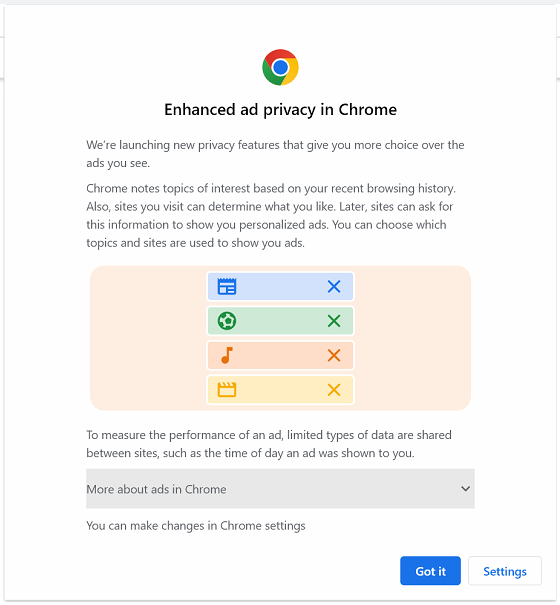
Google Chrome has started prompting for Ad Privacy settings. Instead of just clicking ‘Got It’, we recommend clicking ‘Settings’ so you can opt out.
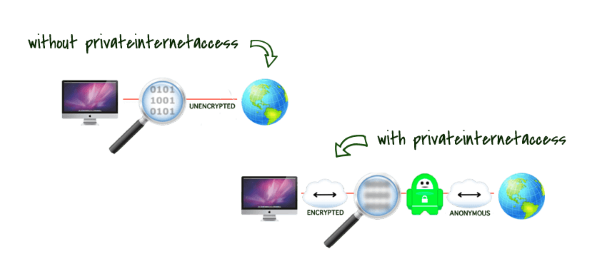
Are you heading to the NARTS conference in San Antonio, TX this year? If so, how you connect to the Internet while you travel, is something you should be aware of – i.e. your connection is likely not secure.

The new Firefox Quantum update is here! I’m writing this post mainly with consignment and resale storeowners in mind.
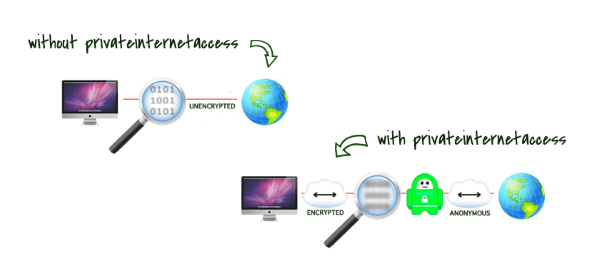
Everything you do on your Internet connection, can be seen by your ISP. That information, while you might not care who sees it, is about to become a commodity to be sold and utilized in ways you might not approve of.