
tl:dr — Watch out for emails from Google regarding your own sign-in activity, as these security emails contain a button that if clicked, will delete all of your App Passwords that allow your consignment/resale software to send email.

tl;dr — As of May 30, 2022, Google no longer supports the Less Secure Apps feature that allowed third party programs (e.g. consignment software such as Peeps’ Software) to be able to send emails. This means, your consignment software likely will no longer be able to send emails from your Gmail account. Going forward, the already-available App Passwords feature in Gmail has to be utilized for sending emails.
As part of Peeps’ Configuration Protocol (our treatment/setup of a Windows machine), we tweak, prune, and better-secure the Windows environment to make it both cleaner, as well as safer for our customers. With Windows 10, the amount of work involved increased exponentially vs. Windows 7. There are so many places Microsoft has added potentially annoying or confusing things.
And as of the latest round of Windows Updates, we’re now seeing the weather appear in the Taskbar:
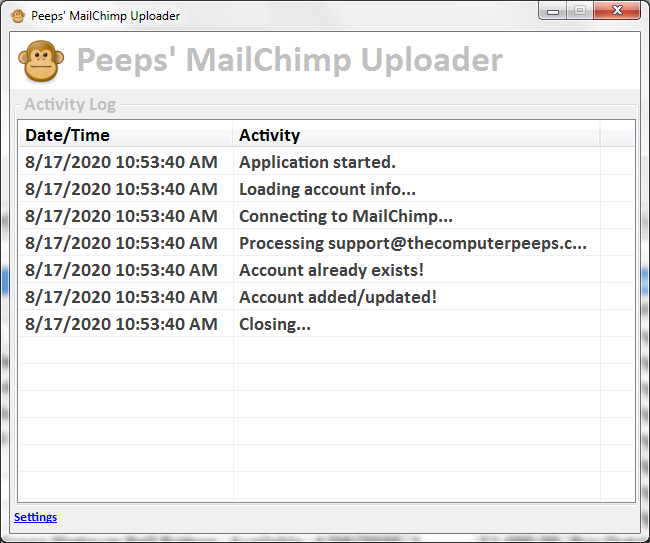
Peeps’ Software integrates with MailChimp, allowing stores to automatically add new consignors and customers to their MailChimp mailing list.
Recently, our app started returning the following error:
Could not create SSL/TLS secure channel