
The Computer Peeps is hiring! Do you know someone who’s awesome? Are you awesome? Call Dean @ (888) 374-5422.
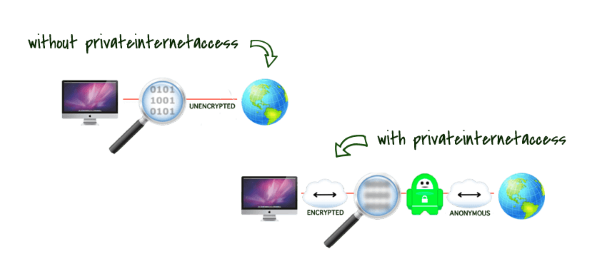
Are you heading to the NARTS conference in San Antonio, TX this year? If so, how you connect to the Internet while you travel, is something you should be aware of – i.e. your connection is likely not secure.

It’s Saturday. You’re not working at your store today, but an employee is opening and running the store for the day. They go to get online and realize there is no Internet connection. They try to use the consignment software on the computers throughout your store, but they get error messages. The credit card system is down too!!!