Are you heading to the NARTS conference in Scottsdale, AZ this year? If so, how you connect to the Internet while you travel, is something you should be aware of – i.e. your connection is likely not secure.
First and foremost, if you connect to a public/free WiFi hotspot, you need to know that all of your network traffic can be captured. There are a variety of things an attacker can do, when he or she has control of your network traffic:
- Trick you into visiting fake, malicious sites.
- Collect your sensitive passwords.
- Collect credit card information.
Even if you’re not on a public WiFi connection, your ISP or whoever manages the connection, can see any website you visit.
If you’re connecting to a network that is not your home or business network, or if you don’t want your browsing activity to be viewable by your ISP, we recommend utilizing a VPN (Virtual Private Network).
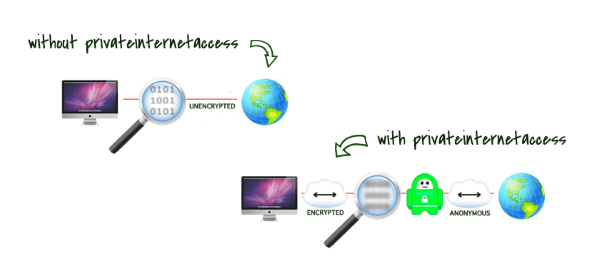
What the heck is a VPN? A VPN creates a secure, virtual ‘tunnel’ across the Internet, through which your network is transmitted. This prevents malicious attackers from seeing your network traffic as you connect to the Internet and other networks.
Which VPN do you recommend?
There are a variety of VPN options out there and a variety of situations to consider, but for a simple, easy, secure connection, we typically recommend Private Internet Access.
They have a great video that explains exactly what Private Internet Access does to keep you protected:
Private Internet Access or PIA, is available for the following platforms:
- Windows
- Mac OS X
- Android
- iOS
PIA is dead-simple to use – just click Connect… that’s it…

PIA alone, is not enough to keep a device secure, but it does provide you with a secure connection when you have to connect to public networks.
What are some other security tips you recommend?
- Prey – Locate your laptop, computers, phones, and tablets if they’re lost or stolen.
- Device/Disk Encryption – If someone gets your laptop — it doesn’t matter if it’s a Mac or PC — all of your files, are fully accessible. It means absolutely nothing if you have a password — all of your files can be viewed and copied directly from your hard drive. There are a variety of disk encryption options out there and we could dedicate a post to just this topic. Newer versions of Android and iOS are encrypted by default. Many mobile OSes allow you to enable encryption, if it’s not enabled by default. There are also 3rd-party encryption programs, such as the final build of TrueCrypt.
- Antivirus – I don’t care if you’re running Windows or Mac OS X, you should be running antivirus, period. If someone tells you otherwise, they’re being cocky and they likely are not personally responsible for your computer’s security. Not just any antivirus either. Stick with one of the top-performing antivirus solutions — we typically recommend ESET NOD32 Antivirus. Whatever you do, do NOT use Microsoft Security Essentials. It does not work and anyone who recommends it, well, they should stop doing that – they’re 100% incorrect.
- Do Not Use Internet Explorer or Safari – Our first recommendation, is Firefox. Some people have been falsely told that “Chrome is the best, install it and you’re secure!” We hope to dissipate that notion. Chrome is definitely a better alternative to Internet Explorer and Safari, however, simply switching to either Chrome, or Firefox, is not enough. You need to be concerned with ad-blocking, Javascript blocking, and malicious changes to your browser, as well as click-jacking. This is why so many Mac users are getting their browser nailed with malware. Instead of letting a website just run whatever it wants in the background (and no, this isn’t stuff you have to enter a password for), you should stop all websites from running anything and only allow websites you truly trust. Right now, you’re letting any website you click, run wild. It’s much better to take the option of NO website can run wild, except for the ones you explicitly trust. This is why we typically recommend Firefox, as the NoScript + uBlock/AdBlock Plus/AdBlock Edge + Public Fox combo is hands-down, the most effective Web Browser configuration @ preventing unwanted downloads or changes in/to the browser itself.
- Do Not Login As Admin/Root – Whether it’s a Mac or PC, it is better to log in as a ‘restricted’ account, instead of a user that has full access to do anything to your system.
As always, if you have any questions, don’t hesitate to call us @ (888) 374-5422.
Featured Image Source: Private Internet Access

