
If your site is built on WordPress, please read this post.
TL;DR – Disable XML-RPC for WordPress.
This past weekend, we started receiving failed login attempt alerts from a few of the WordPress sites we manage. This is abnormal, because all of the sites we manage, are IP-restricted – i.e. You cannot access the login page unless you’re at an approved location, such as your store or home.
So it was definitely, interesting, to say the very least, to start seeing failed login attempts coming in…lots of them (automated via bots/’hacking’ tools):
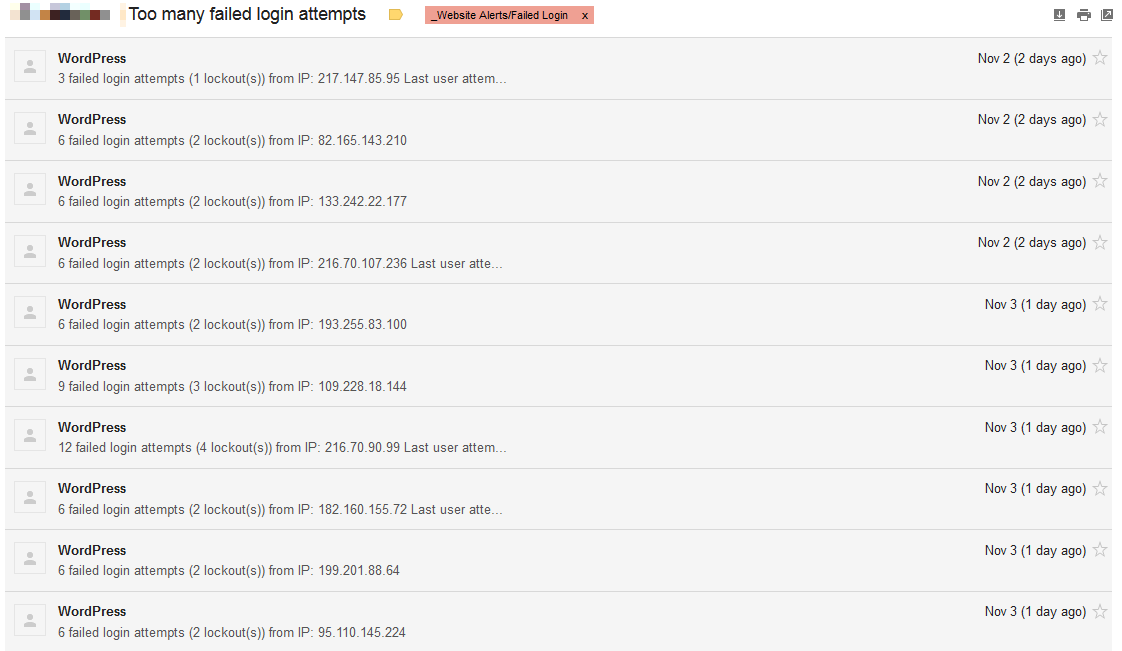
I verified that the sites’ login pages were in fact inaccessible from other IPs. So how the heck were *they* submitting a login? Even a temporary rename of /wp-admin and wp-login.php had no impact, so the logins clearly weren’t coming in through there.
One of the first things that came to mind, were plugins. We only utilize a strict list of plugins and we tend to avoid flooding WordPress sites with random plugins. The sites that were triggering these alerts though, were sites we inherited and did not originally design/build. All plugins are fully managed and updated on a daily basis, so it wasn’t so much an out of date plugin, but possibly one of the odd-ball plugins utilized by a previous developer. There were no consistencies across the sites experiencing this issue though and none of the plugins in question appeared to provide any form of authentication functionality.
What else is ‘listening’ in a WordPress installation? What has its ear against the Internet, waiting for incoming information? XML-RPC, which is utilized for remote publishing from mobile apps and Pingbacks from other blogs.
Sure enough, when inspecting the server logs, I found the offending IPs were in fact submitting /xmlrpc.php:
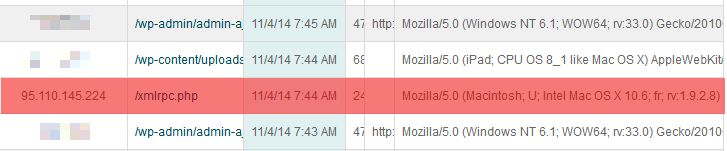
Disable XML-RPC and voila, the login attempts stopped.
This isn’t a new attack, but XML-RPC was disabled by default until WordPress 3.5. It appears that with more and more site owners becoming aware of proper WordPress security and proper Web server security, *they* are looking for other ways in.
Things you can do to better-protect your WordPress site:
- Regularly update your plugins, as well as your WordPress installation. We work with so many store owners who have been paying someone to do this for them, only to find their WordPress site is still running 3.5.1 and plugins have never been updated!
- Install a login limiter, as well as an intrusion detection system for your WordPress installation.
- Properly secure your Web server’s configuration – e.g. disable directory indexing, restrict access for your WordPress login page to only approved IP addresses, restrict access to sensitive configuration files, etc.
- Regularly review your Web server’s logs.
- Disable XML-RPC.
If you have a WordPress site, The Computer Peeps offer a free security audit of your site.
As always, if you have any questions, feel free to comment below or give us a buzz at (888) 374-5422.

